Cookie Preferences
By clicking, you agree to store cookies on your device to enhance navigation, analyze usage, and support marketing.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

We’re asked this weekly: “Should we prioritize ISO 27001/SOC 2 first,or build security first?” Our experience across 100+ conversations with ITand InfoSec leads this year is consistent: security-first wins long-term.You still pass audits—often with fewer surprises—and you actually reduce risk.
Why it matters: mid-market teams don’t have time or budget for parallelreality—one life on paper and another in production. This post explains whychecklists aren’t security, common traps we see, and a step-by-step paththat aligns protection, culture, and compliance. We’ll cover risk management,control mapping, evidence automation, and leadership metrics—using plainlanguage and SME-ready examples.
Ask yourself:
Passing an audit validates that minimum requirements aredocumented and (usually) implemented. It does not guarantee that your mostmaterial risks are reduced. We routinely meet teams who crafted dozens ofpolicies before building workable processes. The real workload starts afterthe first audit—maintaining paperwork that doesn’t match reality, fixingexceptions, and keeping two worlds in sync.
Analogy: You can pass a driving theory test without being a safer driver. Theroad decides, not the paper.
Frameworks (ISO 27001, SOC 2, TISAX, NIST CSF) are valuable scaffolding.But they update slower than change in your environment—think of howquickly AI tools entered daily workflows. If your program is driven by a staticcontrol list, emerging risks fall through the cracks. The intent ofthese frameworks is risk-based improvement; the practice too often becomescheckbox execution.
Behavior is shaped more by mindset and incentives than by PDFs.This year several leaders told us: “We passed the audit; management’s happy—butthe structural gaps remain.” Policies no one reads don’t move the needle.Short, role-based training and simple reporting channels do.
Identify top risk scenarios in the language of the business(e.g., “Invoice fraud via compromised mailbox,” “Ransomware halting productionfor 48 hours,” “Unauthorized AI data leakage”). Score by impact and likelihood;note crown-jewel systems and data flows. Controls come after scenarios,not before.
Scenario → Impact → Likelihood →Existing safeguards → Gaps → Owner → Next step (30/60/90 days)
For each risk, place the control where work happens:
When controls live inside the workflow, people comply by default,not by remembrance.
Prefer tools and processes that emit logs and approvals automatically(ticket comments, recorded reviews, CI/CD checks, MDM baselines). This preventsa parallel “audit binder” and keeps the evidence authentic and low-effort.
Replace “% controls implemented” with 5–7 vital KPIs tied to riskand outcomes:
These metrics make progress visible and drive decisions.
A services company drafted a fullISMS before operational changes. They passed ISO 27001, but spent the next 12months reconciling documents with reality as teams resisted impractical steps.After pivoting to risk-first, they embedded approvals in finance, automated MDMreporting, and cut audit prep time by 60%.
A manufacturer adopted multipleAI assistants at team level. Their framework-driven checklist didn’t mention AIspecifically, so risks went unaddressed. A targeted review mapped data flows,added role-based guidance, red-teamed prompts for leakage scenarios, andintroduced a controlled model with logging—closing the gap before the nextreview.
An engineering org replaced a25-page “secure coding policy” with a 2-page role guide, mandatory PRtemplates, and quarterly clinics. Vulnerabilities per release dropped, andevidence came straight from the pipeline.
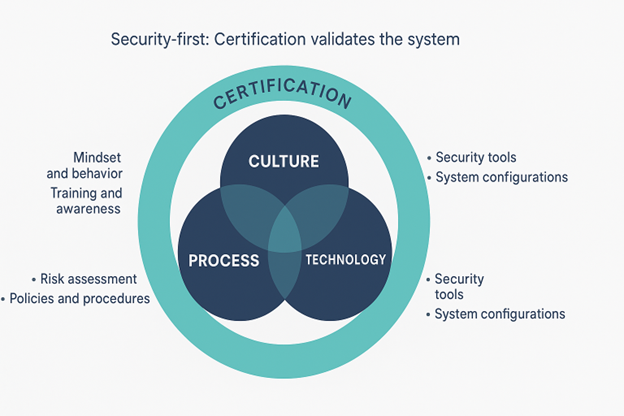
Certifications can unlock deals, strengthen trust, and providestructure. But they are a cross-check, not the driver. Not every SMEneeds a certificate immediately; everyone needs security that matchesrisk and maturity. When security leads, audits typically require only lightdocumentation polish, not heroic catch-up.
"Ipsum sit mattis nulla quam nulla. Gravida id gravida ac enim mauris id. Non pellentesque congue eget consectetur turpis. Sapien, dictum molestie sem tempor. Diam elit, orci, tincidunt aenean tempus."
If speed is mandatory (customer deadline): get targeted support thatbalances a fast pass and a realistic roadmap—so Day 2 doesn’t become Day0 all over again.
Real security isn’t a checklist—it’s the compounding effect of clearrisks, workflow-embedded controls, and habits your people can sustain; when youbuild that foundation, audits become validation rather than a scramble. If thisresonated, you might also like our related reads: “What Is AuditTheater—and How to Avoid It,” “ISO 27001 vs. SOC 2 for SMEs,” and “AIin the Workplace: A Risk-First Checklist That Actually Works.”
Should we do ISO 27001 first or build security first?

If we pass an audit, aren’t we secure?

How do we avoid “audit theater” and still be audit-ready?

What KPIs should leadership actually track?

Do frameworks cover new risks like AI data leakage?

Certification validates a security-first system built on Culture, Process, and Technology—it's the ring around the core, not the core itself.
With 10+ years of experience, helps SMEs turn compliance noise into risk-based outcomes with workflow-embedded controls and self-generating evidence.
Learn how to design a security-first program that reduces risks, builds culture, and still clears ISO 27001 and other audits, without turning your team into paperwork managers
Read More